Authentiek vakmanschap voor houten poorten
Al sinds de opstart meer dan twintig jaar geleden specialiseert Poorten Pauwels zich uitsluitend in houten tuinpoorten en opritpoorten. Peter Pauwels en zijn opvolger Arne Pauwels voeren nog elke plaatsing zelf uit. Deze persoonlijke aanpak vormt samen met de hoge specialisatiegraad uw beste kwaliteitsgarantie.
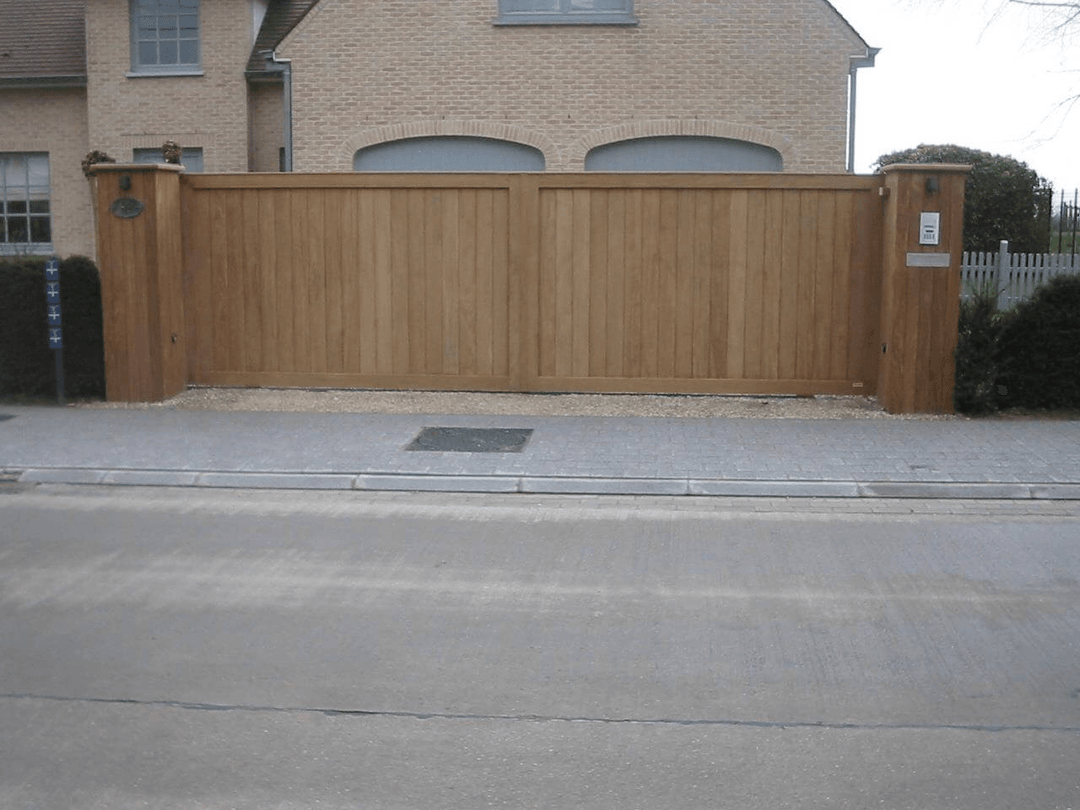
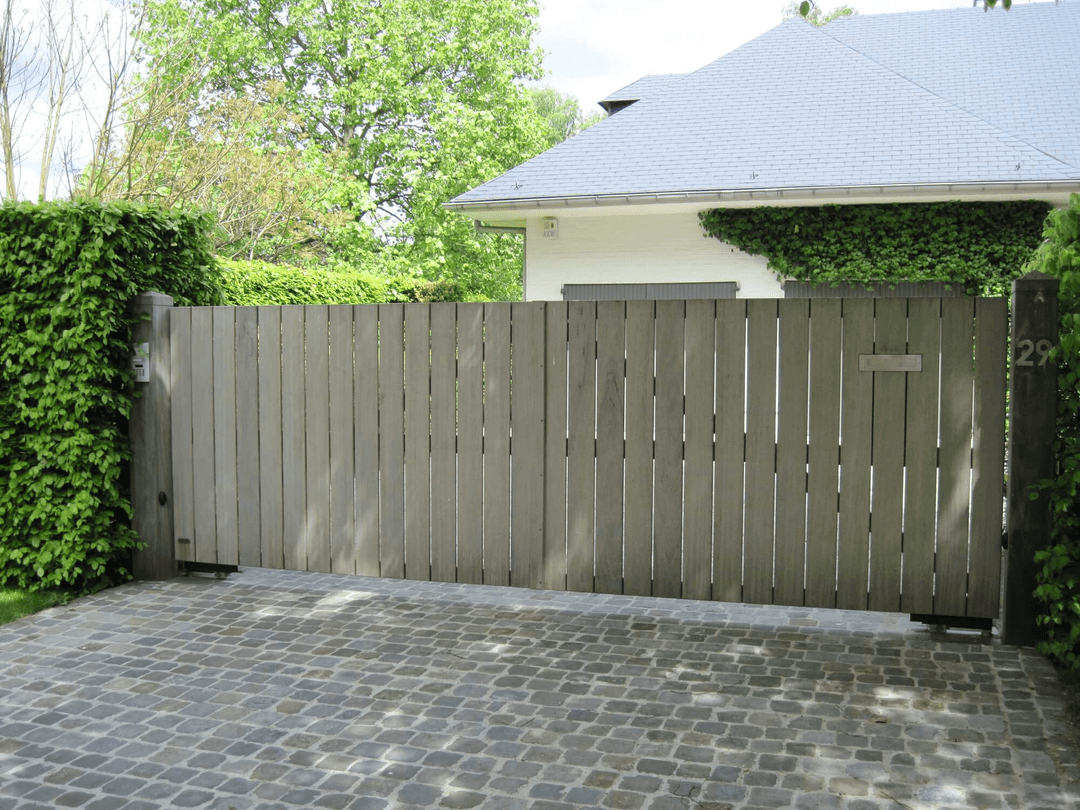
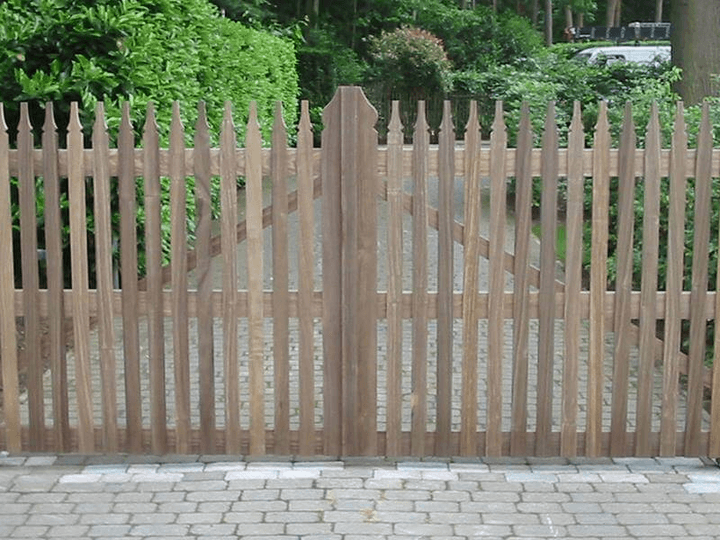
Wij staan garant voor maatwerk tuinpoorten in afrormosia of padouk in combinatie met authentiek vakmanschap. Elke poort wordt vanaf het ruwe hout met de hand gemaakt in onze eigen schrijnwerkerij in Lille-Wechelderzande.
Onze referentielijst telt inmiddels meer dan 3.000 tevreden klanten. Elke houten tuinpoort wordt volledig op maat gemaakt volgens de wensen van de klant. Vrijwel alle afmetingen zijn zowel in draai- als schuifvorm mogelijk. Alleen het beste tropisch hardhout is goed genoeg. Zo verzekeren we uw houten poort van de beoogde lange levensduur.